How to prevent phishing attacks in your organization?
News | 13.01.2023
What is phishing?
Phishing is a social engineering attack that is used for stealing user data such as credentials, credit card numbers, ´passwords, etc. Attackers apply various techniques to trick their victims, e.g. by imitating websites, e-mails or forms of familiar services like banks or streaming-providers.
The most popular phishing techniques
Email phishing
Email phishing is the most common attack. The attacker uses customized email campaigns to imitate a brand that is trusted by users.
See the example of an email phishing attack that was created by an attacker with masking by FedEx. The attacker used the corporate style of FedEx, including logo, fonts colors, etc.
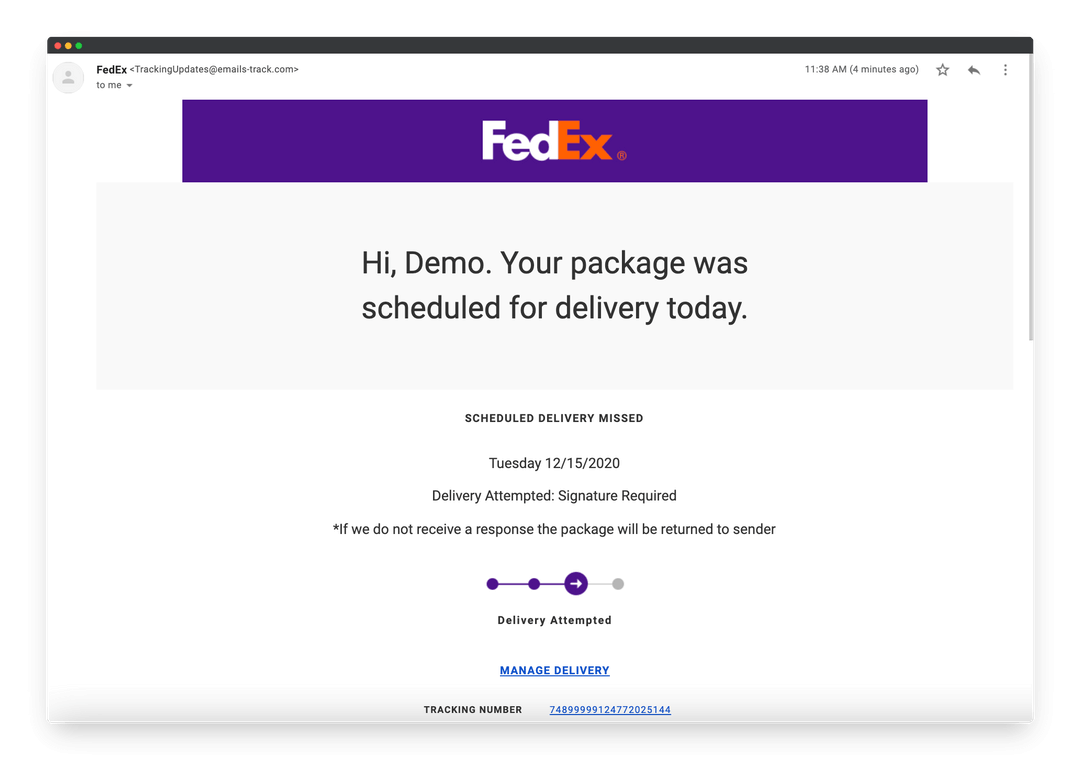
For example, a letter is sent to you “*If we don’t receive a response the package will be returned to sender” and an expiration date. Applying such pressure causes the user to be less diligent and more prone to error.
Spear phishing
Spear phishing is a type of phishing attack that focuses on a specific company or person. For this, the attacker learns all about the company, its employees, and its processes and creates a personal attack chain that is maximally adapted to the organization's processes.
Let's look at an example of a spear phishing attack. The attacker sends an email to the head of the department with the subject line: “Updated invoice.” The text, style, and included logo duplicate the organization's email template.
The link in the email redirects to a password-protected internal document. The manager is asked to login into the system to view the document. The attacker steals credentials and gets full access to corporate systems on the organization's network.
Another phishing technique is known as CEO Fraud — It's a type of spear phishing that imitates famous people's profiles, usually CEO or public figures.
Business Email Compromise (BEC)
This is also known as Email Account Compromise (EAC) attack, and is one of the most dangerous subcategories of spear phishing targeted at a company. The BEC only consists of text, which helps to mask itself in normal traffic. Some BEC attacks integrate into the middle of an existing email chain and most often, an attacker imitates a C-Level manager of the company.
Brand Spoofing — an attacker uses brand awareness to get confidential data.
Clickjacking — an attacker lures the user to a webpage with embedded malicious code that catches confidential information or access to the user's computer.
Pharming — Typically, an attacker runs malware on users' computers that redirects to phishing sites.
Evil twin — the attacker duplicates a wireless access point that users connect to by transferring confidential data.
How to prevent phishing attacks in your organization?
Train users.
Security awareness training and a simulated phishing platform can teach employees to make smarter security decisions. This type of solution includes security learner content, a service for simulation attacks with measurement capabilities of results.
We recommend testing solutions of Softprom partners KnowBe4, CybeReady, SimSpace (for the cybersecurity team).
|
Security Awareness And Training Solutions |
KnowBe4 | CybeReady |
|---|---|---|
| Security awareness training content | + | + |
| Simulated phishing attacks | + | + |
| Learner content on the multiple languages | + | + |
| Branding content | + | + |
| Learning management system (LMS) for creating own content | + | + |
| Metrics and measurement capabilities | + | + |
| Risk quantification (identify risk at the user) | + | + |
| AI-driven phishing | + | + |
| Responses and interventions | + | + |
| Administration and support | + | + |
| Reporting capabilities | + | + |
Anti-phishing solutions.
Anti-phishing solutions scan the content of incoming and internal email messages, links, and attachments in messages on potential phishing or impersonation attacks. Anti-phishing services can also use DNS authentication and DMARC, DKIM, and SPF protocols to detect potential authentication issues.
We recommend review solutions Barracuda Email Security Gateway, BrandShield Anti-Phishing Solutions, Forcepoint Email Security, ImmuniWeb Discovery, RedSift OnDMARC, ThreatMark Anti-Fraud Suite and etc
Softprom — Value Added IT Distributor provides a full cycle of support at all stages of the sale: presale, piloting, implementation, training, and technical support.
If you have a question about a solution, need pricing information for your project calculation, or assistance in implementation by our certified engineers, please write or call to Softprom.







