About company
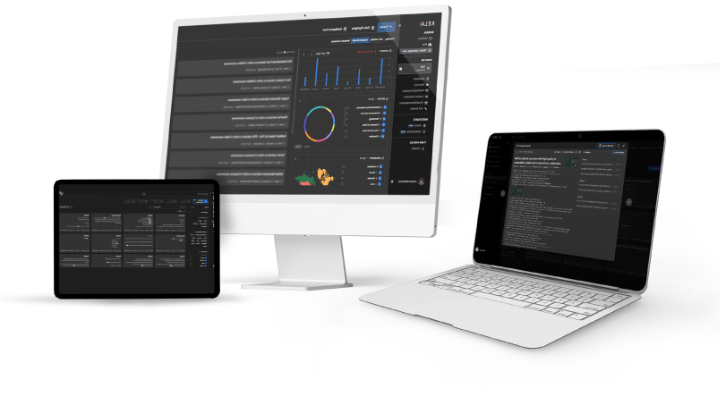
KELA’s tailored threat visibility, combined with cybercrime attack surface intelligence, arms you with highly contextualized intelligence, as seen from the eyes of attackers, thus enabling proactive network defense.
Softprom promotes and distributes KELA's solutions in the European Union, Switzerland, Armenia, Azerbaijan, Georgia, Kazakhstan, Kirghizia, Moldova, Ukraine, Uzbekistan, Tajikistan and Turkmenistan.
KELA Cyber Intelligence Platform include four products
INVESTIGATE
The module helps investigate and analyze threats, targets, topics, and groups, anonymously and in real-time to perform successful threat hunting and deepen their cyber investigations with contextualized intelligence insights as to attackers’ TTPs, threat actor profiles and identities, hacking discussions, and more
MONITOR
The module supports monitoring cybercrime sources for essential organization assets, providing attack surface and asset management capabilities. It alerts on targeted threats specifically aimed at the organization by analyzing the adversary’s perspective of its external attack surface and maintaining proactive network defense
TECHNICAL INTELLIGENCE
The module monitors the latest compromised network assets that can be exploited by threat actors for their next cyber attack. Such assets can be abused to serve as an attack infrastructure or as an attack vector such as phishing attacks, (for example, as a C2 server)
THREAT LANDSCAPE
The module offers decision-makers high-level intelligence on the ever-changing cybercrime ecosystem, including dashboards of top trends, daily highlights, and finished intelligence feed by KELA’s cyber intelligence experts. It includes ransomware events, network access on sale, leaked databases, and new threats across all sectors to deliver high-level executives with effective, strategic information, thus enabling informed decisions on the next steps
Countries
Softprom is the official distributor of this vendor in the territory of







 Albania
Albania Armenia
Armenia Austria
Austria Azerbaijan
Azerbaijan Bosnia and Herzegovina
Bosnia and Herzegovina Bulgaria
Bulgaria Croatia
Croatia Cyprus
Cyprus Czech Republic
Czech Republic Estonia
Estonia Georgia
Georgia Germany
Germany Greece
Greece Hungary
Hungary Kazakhstan
Kazakhstan Kosovo
Kosovo Kyrgyzstan
Kyrgyzstan Latvia
Latvia Lithuania
Lithuania Moldova
Moldova Mongolia
Mongolia Montenegro
Montenegro North Macedonia
North Macedonia Poland
Poland Romania
Romania Serbia
Serbia Slovakia
Slovakia Slovenia
Slovenia Switzerland
Switzerland Tajikistan
Tajikistan Turkmenistan
Turkmenistan Ukraine
Ukraine Uzbekistan
Uzbekistan