WHY TRIPWIRE?
News | 03.07.2020
THE MOST TRUSTED PRODUCTS IN CYBERSECURITY
Our solutions work on-site and, in the cloud, to find, monitor and minimize a wide range of threats without disrupting daily operations or productivity. Think of us as the invisible line of defense that keeps systems safe.
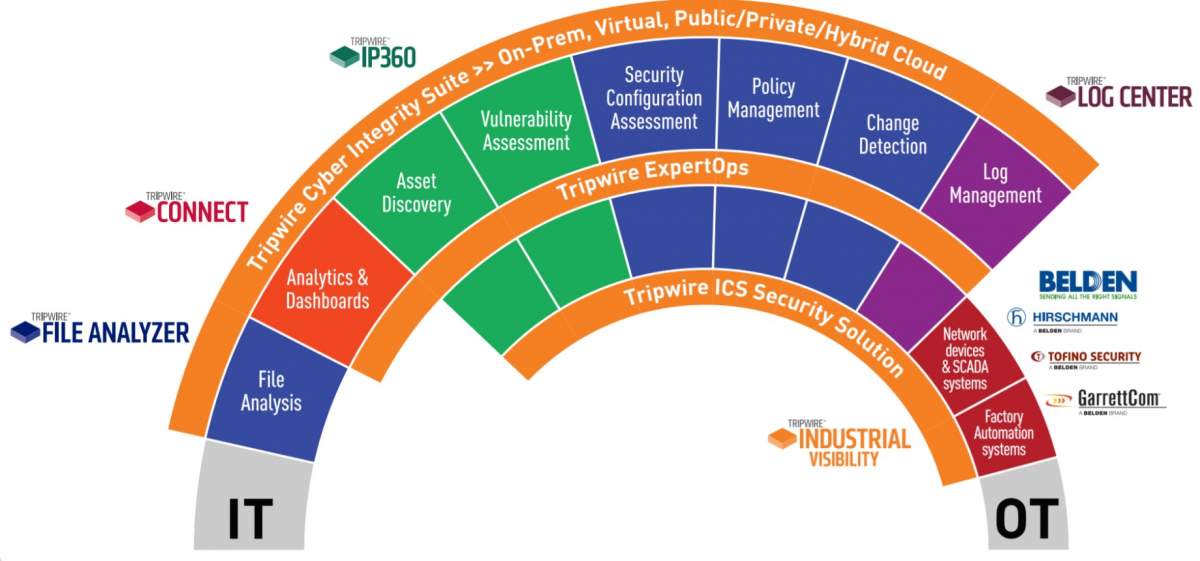
Tripwire Enterprise
Tripwire Enterprise is the industry’s leading security configuration management (SCM) solution. Tripwire Enterprise responds to cyber threats in real time and prevents future attacks.
Tripwire Log center
Simplify Event Monitoring with Tripwire Log Center. Complete, secure, reliable log collection that highlights events of interest from a sea of data.
Tripwire IP 360 tools
You can't manage what you can't see. Discover and profile every device and software component on your network across your hybrid environment, including on-premises, cloud, and container-based assets. Locate previously undetected assets using both agentless and agent-based scans
Tripwire ExpertOps
Choose Tripwire ExpertOps SCM for File Integrity Monitoring & Security Configuration Management. Get the maximum-security benefits of industry-leading FIM and SCM right away with Tripwire ExpertOps SCM.
Tripwire Analyzer
Tripwire File Analyzer extends the capabilities of Tripwire Enterprise with fully integrated detection of known and zero-day exploits through deep file inspection and analysis.
Tripwire for DevOps
Tripwire for DevOps integrates into your organization’s CI/CD pipeline to provide seamless pre-deployment assessment of images. Tripwire for DevOps discovers vulnerabilities, misconfigurations and policy violations in containers and virtual images, returning results directly back into development tools.
While each product in the Tripwire portfolio provides valuable capabilities in a stand-alone implementation, customers receive maximum value when they are integrated—with each other or with third-party products—to achieve faster and more accurate security and compliance in both IT and OT environments.
Tripwire integrates with a wide array of third-party products to offer a multitude of benefits and use-cases in these distinct categories:
- Threat intelligence
- Network security
- Analytics and security information and event management (SIEM)
- IT service management (ITSM)
- Integrated access management (IAM)
- Industrial control systems (ICS)
- Factory automation systems (FAS)