What is cryptojacking? New threat from old "friends".
Reportage | 23.11.2021
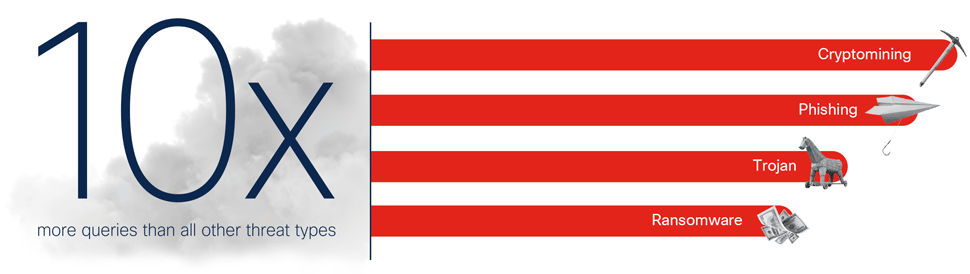
In the 2021 Semi-Annual Vulnerability and Threat Trends Report, the Softprom team found that the number of malware exploiting new vulnerabilities grew by 20% compared to the first quarter of 2021 in almost all categories, from ransomware to botnets and Trojan attacks. However, cryptojacking has climbed the malware rankings faster than Netflix's movie Squid Game in charts.
There are several reasons for this explosive growth in popularity.
The first reason - Bitcoin set a record for capitalization in 2021.
Research shows that malicious attackers are not just attackers - they are savvy “entrepreneurs”. So, if you think that only idiots and lazy people are engaged in the cryptocurrency business, and they never have enough skills to sneak through your security system, we hasten to upset you - you are naive. These attackers have a business plan, tools, and processes to launch attacks designed to exploit vulnerabilities and profit from your gullibility. Crypto mining is a profitable business, and this should alert you.
The second reason why cyber fraudsters have become more active is that “gold miners” do not have enough tools.
Today, a major constraint in the cryptocurrency business is the lack of computing power needed to mine bitcoins and most other cryptocurrencies. How to influence this process in the phase of a shortage of microcircuits and a drop in output due to COVID - cybercriminals poach computing power inside corporate networks using ready-made exploit kits designed for mining cryptocurrencies. In some cases, malware-as-a-service providers lease botnets of already infected machines to crypto miners.
Psss ... Buddy. Do you want to rent a mining rig to profit from these suckers?
Crypto mining and ransomware are not only two of the fastest-growing categories of malware - they also exploit a wide variety of vulnerabilities; more than all other categories of malware combined. By creating programs that exploit multiple vulnerabilities, malware vendors can serve a wider range of customers with a single product. These versatile programs are like Swiss army knives, versatile tools that can be used for a variety of purposes.
The trend is clear - malware creators are discovering new vulnerabilities and actively developing new malware to take advantage of the latest vulnerabilities. This is often achieved by simply tweaking existing malware to execute new exploits. Essentially, malware evolves like viruses, with new variants emerging in response to a changing environment.
Crypto mining has another impact on business. Unfortunately, this poses a cybersecurity threat. In a process known as cryptojacking, cybercriminals use malware to covertly gain control of your computers, smartphones, and servers. From there, they can use the processing power of your device as part of their overall crypto mining operation.
Since miners are running in the background, you might not notice them. However, the consequences are devastating. Your processing power is busy, so your computer is slowing down. Plus, you'll pay extra electricity bills to keep the software running while someone else makes a profit. Nobody wants to fall prey to a parasite.
In response to the threat of cryptojacking, businesses must not only better prevent infection, but also implement and enforce policies that lockdown infected machines and prevent further data leaks. This is a set of measures for identifying potential entry points for attackers, ensuring the proper configuration of network devices, and controlling access to the network.
The Softprom team keeps abreast of new challenges and offers many solutions to ensure your reliable protection. One of these solutions is a software package with "instant" payback from Skybox Security.