Lepide LepideAuditor
Insider Threat Detection Software
An insider may attack your critical servers or sensitive data for any number of reasons, malicious or otherwise, causing potentially severe damage to both the reputation and the bottom line of the business. Insider threats are often harder to defend against than external ones since the majority of insider threats are completely unintentional. The best way to combat them is to adopt strict security measures. Pro-active auditing of your IT infrastructure in order to track user activities and monitor configuration changes is of the utmost importance in the fight to minimize insider threats.
- Discover and Classify. Determine where your sensitive data is and why it is sensitive. Tag, classify and score that data based on the content
- Deep Permissions Analysis. Find out who has access to your data and how it was granted, so that you can ensure proper data access governance
- User Behavior Analytics. Find out what your users are doing with your data and whether the changes they are making are affecting your security
- Spot Anomalies. Get instant notifications when users are making changes they have never made before, including single point anomalies
- Detailed Reporting. Hundreds of pre-set reports related specifically to security and data access governance challenges
- Real Time Alerts. Get alerts delivered straight to your inbox or mobile when potentially harmful changes are being made
Insider Threat Detection Made Simple
LepideAuditor helps give you the visibility that you need to detect and prevent insider threats. You will be able to identify where your sensitive data is, who has access to it and what your users are doing with it.
Spot Anomalies in User Behavior
Our sophisticated anomaly spotting technology will help you detect when users are making changes to data that could be seen as anomalous. When such changes are made, you can be notified in real time or through pre-defined reports. We are even able to detect single point anomalies, to give you invaluable insight in the behavior of your users in relation to your data.
Proactively Monitor Potential Insider Threats
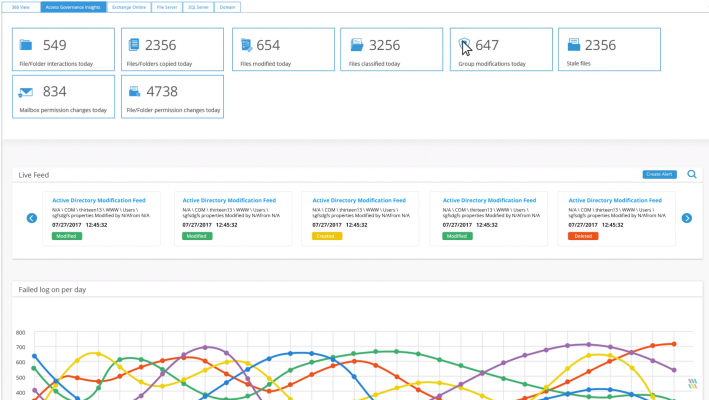
Many organisations will only start to feel the effects of an insider threat once data has been leaked and it is too late to do anything about it. The only way to ensure that this does not happen is by adopting a pro-active and in-depth auditing strategy. LepideAuditor allows administrators to add single or multiple instances of Active Directory/Group Policy Objects, Exchange Server, SharePoint Server, SQL Server, File Server, Office 365 and Dropbox. The solution provides enterprise-wide visibility on these server components through a single powerful, easy-to-use console. You can browse through graphical Radar Tabs and generate over 270 pre-defined reports to give you complete visibility into changes being made.
Real Time Alerts for Critical Changes
Critical changes taking place in your systems could be affecting your organisation in adverse ways. If left unnoticed then these changes could be extremely damaging to the reputation and bottom line of the business. LepideAuditor plays an important part in detecting critical changes the instant they occur. It sends real-time alerts via email, as an update to its Radar Tab and as a push-notification to the LepideAuditor App (available on all Android or Apple smartphones).
See Who is Accessing Your Data
Whenever privileges are granted, the first step an insider may take is to access critical data. You should know in real-time who had accessed business-related files and folders and what changes users have made to them. There are multiple reports in LepideAuditor that help you identify access attempts made by users to the data stored in Exchange Server, File Server, SQL Server and SharePoint. If a user tried to access the mailbox of another user, for example, the administrator would receive a real-time alert as an email and as a notification in the LepideAuditor App.