Breach and Attack Simulation Platform
Fully automated and customizable, Cymulate challenges your security controls against the full attack kill chain with thousands of simulated cyber attacks, both common and novel.
An awards-winning SaaS-based Breach and Attack Simulation (BAS) platform makes it simple to know and optimize your security posture any time, all the time.
Fully automated and customizable, Cymulate challenges your security controls against the full attack kill chain with thousands of simulated cyber attacks, both common and novel. Testing both internal and external defenses, the attack simulations show you exactly where you’re exposed and how to fix it-making security fast, continuous, and part of every-day activities. With 360° visibility and actionable reporting, Cymulate shortens test cycles and offers a counter-breach assessment technology that empowers security leaders to validate the effectiveness of their current security controls by taking a proactive approach to their cyber stance, so they can stay one step ahead of attackers.
How Cymulate works
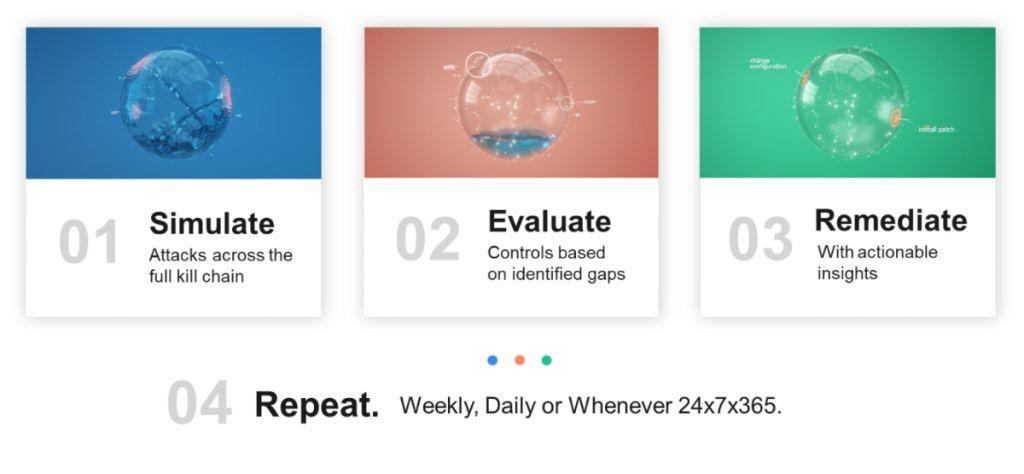
Cymulate lets you improve your security posture 24X7X365 within minutes, in just three simple steps:
Key platform capabilities
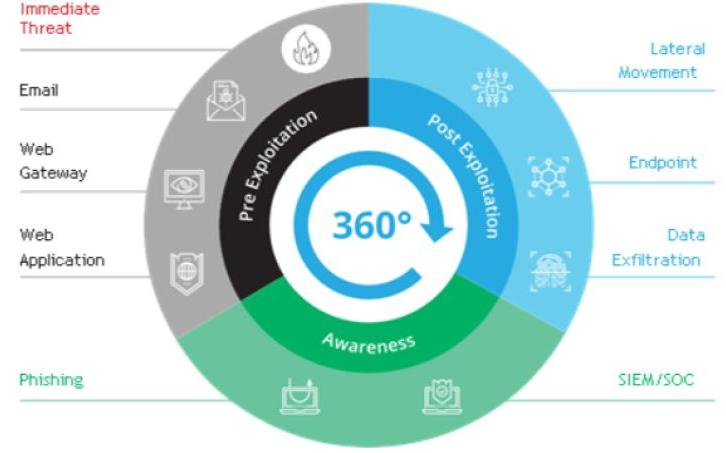
- Tests defenses against the full attack kill chain. We’ve divided the attack surface into nine vectors that can be run ‘a la carte or simultaneously to simulate a full Advanced Persistent Threat (APT). Challenging both internal and external (perimeter) security controls, Cymulate’s attack simulations replicate the modus operandi of real-world threat actors in a safe manner, running the full gamut of cyber threats, from ransomware to banking Trojans, SQL injections and countless others.
- Attack customization tailored to your needs. By easily customizing attacks to test security controls against specific threats or threat components, assessments become much more efficient and time-toremediation is shortened.
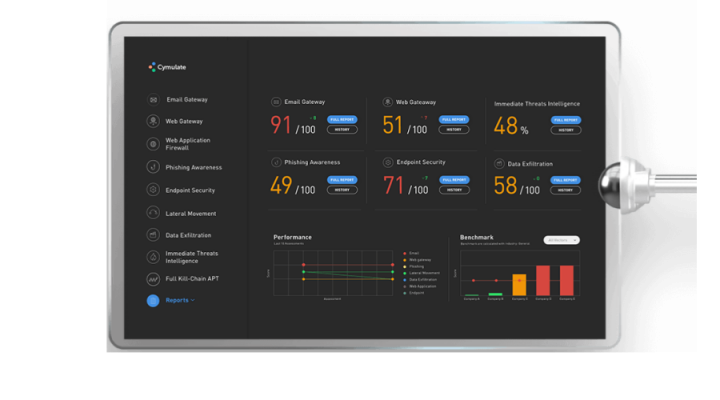
- KPI-friendly metrics and benchmarking. After running an assessment, a score is generated, reflecting the magnitude of potential threats to target systems or resources, with industry-specific benchmarking. Cymulate’s risk score is calculated using industry standards such as the NIST Risk Management Framework, CSVSS v3.0 Calculator, Microsoft’s DREAD and the MITRE ATT&CK Framework.
- Comprehensive reporting and alerting. Instrumental to meeting compliance mandates and demonstrating ROI,a technical and executive summary are generated at the end of each assessment. Alerts can be generated to notify personnel when the Cymulate Risk Score exceeds a certain threshold.
Features
Deploys in minutes
Simple to use
Single agent, unlimited attacks
SaaS-based platform
Automated or on-demand
Very latest threats simulated with a few clicks
Covers the full attack kill chain
Video
[Webinar Recording] Cymulate | Attack Simulation in Action
Which CyberSecurity product protects your company best?