Attack Surface Management
Bugcrowd External Attack Surface Management (EASM; formerly Informer EASM) offers a complete, accurate view of your external risk exposure. It continuously scans and maps your digital footprint – including web domains, subdomains, IPs, and cloud services – and tracks changes over time, providing valuable intelligence for enhanced human-driven testing.
Bugcrowd EASM is complemented by ASM Risk offering, which engages hackers with elite recon skills to discover and prioritize asset risk and packages results in an Executive Report.
- Map your assets. Gain an attacker perspective by discovering known and unknown assets to create a detailed map of your external attack surface.
- Monitor for changes. Continuously scan your applications and infrastructure to detect changes and exposures that need action.
- Get actionable insights. Use email alerts, customizable reports, and JIRA notifications to give stakeholders the information they need for fast remediation.
- Amplify security testing impact. Combine intelligence from Bugcrowd EASM with penetration and crowdsourced testing on our platform for risk reduction and cost savings.
Discover, identify, and secure digital assets
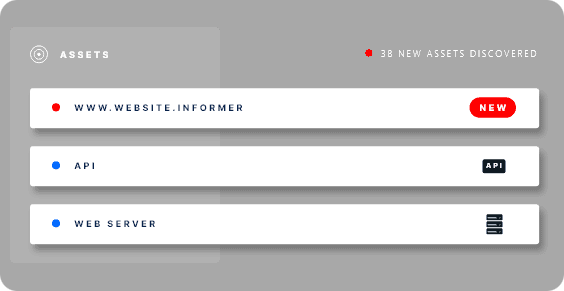
Bugcrowd EASM uses active scanning and accesses hundreds of data sources to identify all of your digital assets in seconds, using a single seed domain as the starting point. It continuously monitors your online environment (delivering instant alerts about risks and changes), creating a complete view of your external attack surface.
Add your cloud services to scope
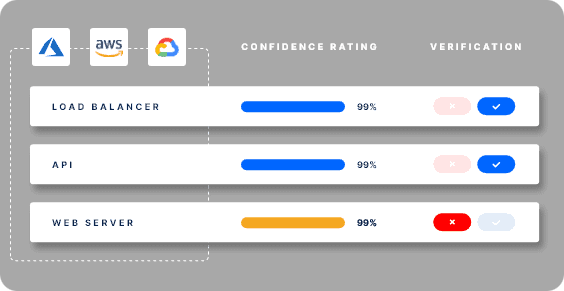
Bugcrowd EASM helps you keep up with fast-changing cloud environments, where new resources are created and deleted frequently. Easily connect to your AWS, Azure, or Google Cloud infrastructure with a few clicks to get real-time insights about your externally facing assets – including load balancers, app engines, and data stores.
Find, manage, and prioritize risk
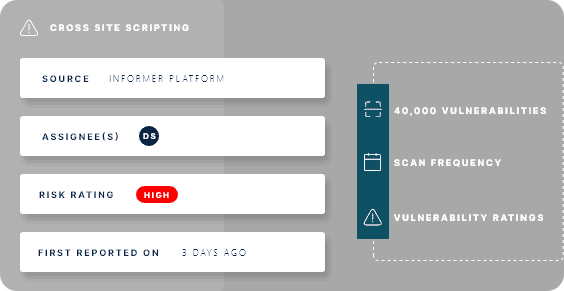
With Bugcrowd EASM, you can continuously scan your assets for over 40,000 application and infrastructure vulnerabilities. Schedule scans based on risk exposure – daily, weekly, or monthly. Each vulnerability is automatically assigned a CVSS rating so you can accurately prioritize remediation. Finally, automated regression testing validates your fixes.
Features
The ability to detect and map all organizational assets (both known and unknown) to create a detailed view of potential attack points.
Continuous monitoring and scanning of assets to identify changes that could impact security, and taking timely measures to address them.
Integration with various alerting and reporting systems so that stakeholders can quickly receive critical information and take action to mitigate vulnerabilities.
Integration and combination of security data with various testing methods to improve efficiency and reduce security costs.