Attacks on root DNS servers: analyzing the resilience of global infrastructure
News | 09.01.2026
The Internet is a system of systems. There is no central committee that governs how it is built and operated. However, there are several subsystems that are critical to the secure functioning of the entire network. One of them is the root servers of the Domain Name System (DNS). If the DNS root system were to become unavailable, it would be practically indistinguishable from a complete Internet shutdown.
The DNS root system has been repeatedly attacked throughout history, and in some cases, partial failures have been observed. Nevertheless, it remains resilient thanks to replication, redundancy, and a high level of operational management. In this article, we will examine the pressure the root system faces from DDoS attacks, based on data from the ASERT team at NETSCOUT.
Key Research Findings
- The DNS root server system possesses high availability and resistance to attacks.
- The DNS Anycast mechanism is a key factor in the system's survival.
- Root servers encounter significant volumes of flood and parasitic traffic daily.
- Different instances of root servers can receive substantially different volumes of traffic.
Types of DNS Attacks
DNS attacks are generally divided into two main types:
Data Integrity Breach
- Server compromise and alteration of zone files.
- Manipulation of the name resolution process "on the fly" (e.g., DNS cache poisoning).
Denial of Service (DoS)
- An attempt to disable an authoritative DNS server. The higher the server's level in the name hierarchy, the broader the consequences of the attack.
The ATLAS Visibility Platform Provides a Colossal Volume of DDoS Attack Event Telemetry
The chart below presents a chronological overview of events targeting root servers.
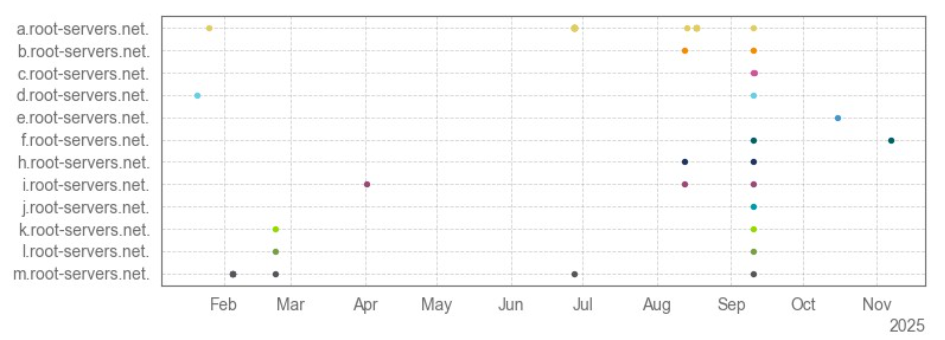
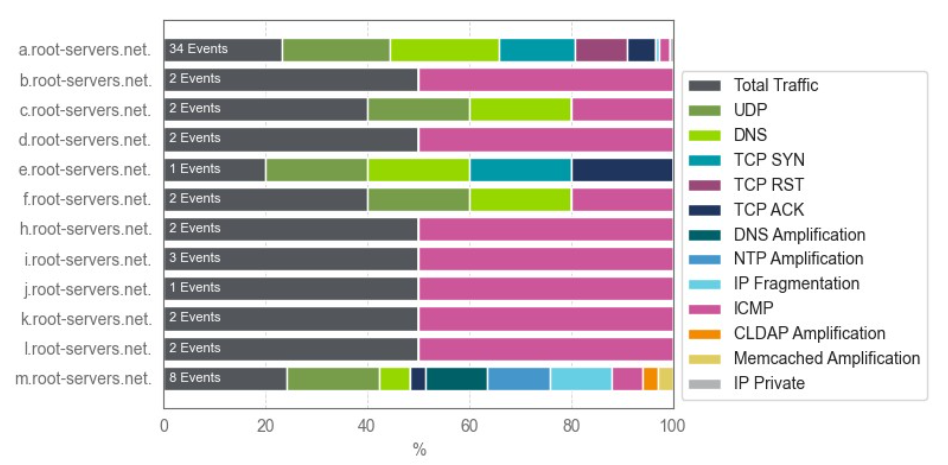
ASERT experts observe various attack vectors. For example, "A" and "M" servers encounter numerous types of DDoS vectors, while other servers more frequently see combinations of general traffic and attacks via the ICMP protocol.
Why Is Server "A" Targeted Specifically?
There are several reasons why the load is distributed unevenly:
- Topological Proximity: BGP Anycast routes requests to the nearest node, and some instances naturally attract more traffic.
- Historical Factor: Server "A" is often attacked simply because it is the first letter of the alphabet—a simple but probable reason.
The figure shows a percentage overview of observed DDoS events, illustrating the distribution of vectors across servers.
Comparison: Traditional Defense vs. NETSCOUT Approach
Traditional Firewalls
- Priority: Stateful inspection.
- Problem: They often become a "bottleneck" during massive DNS floods, failing under load before the application itself.
NETSCOUT Arbor + AIF Solution
- Priority: Stateless filtering and adaptive protection.
- Advantage: Utilizing global ATLAS analytics to automatically block known attack sources at the perimeter.
Softprom Recommendation: ATLAS Intelligence Feed Technology
The issue of attacks on root servers demonstrates how vital it is to have real-time threat data. For corporate DNS infrastructure, we recommend using the ATLAS Intelligence Feed (AIF) from NETSCOUT.
AIF is not just a data stream, but a deeply curated knowledge base that:
- Automatically arms Arbor Edge Defense (AED) devices with current Indicators of Compromise (IoC).
- Provides "Adaptive DDoS Protection" that learns from global traffic (over 800 Tbps) visible to NETSCOUT worldwide.
- Enables blocking of not only inbound floods but also outbound communications from infected devices to botnet command-and-control centers.
Understanding what the "root" of the internet sees is a harbinger of what any organization may face tomorrow.
Softprom is a Value Added Distributor of NETSCOUT. Need help protecting your infrastructure from DDoS? Our experts are ready to provide technical support and conduct a pilot project. Learn more about NETSCOUT solutions or contact us to request a personal consultation.







