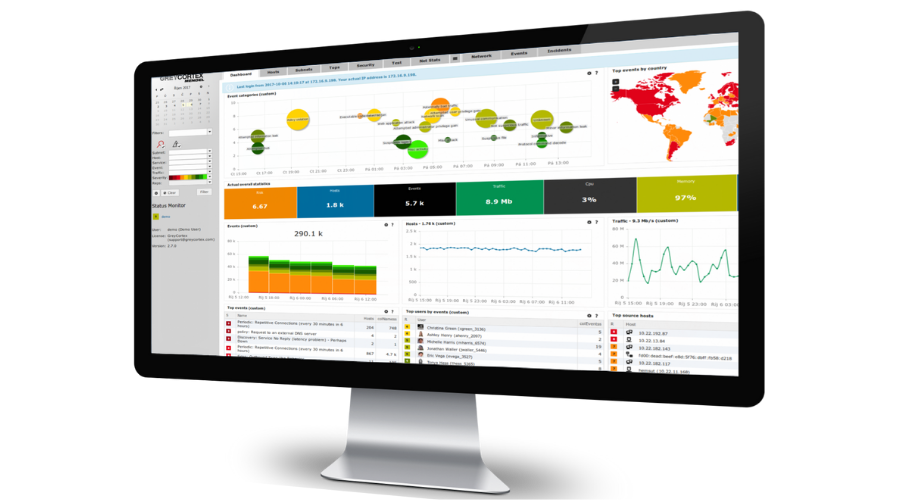
GREYCORTEX Network Detection and Response (NDR)
GREYCORTEX Mendel is a cutting-edge Network Detection and Response (NDR) solution designed to provide comprehensive visibility and advanced threat detection across both IT and operational technology (OT) networks.
GREYCORTEX Mendel is a cutting-edge Network Detection and Response (NDR) solution designed to provide comprehensive visibility and advanced threat detection across both IT and operational technology (OT) networks. Leveraging AI and machine learning, Mendel continuously monitors network traffic to identify known and unknown threats, including zero-day attacks, ransomware, and insider risks. With easy deployment, robust forensic capabilities, and seamless integration with existing security infrastructure, Mendel empowers organizations in critical industries like energy, healthcare, manufacturing, government, and finance to strengthen their cybersecurity posture and ensure uninterrupted operations.
GREYCORTEX Mendel is engineered to tackle the multifaceted security and operational challenges faced by organizations today, offering a comprehensive suite of capabilities:
Comprehensive Network Visibility
- Gain a clear, real-time understanding of all connected devices, their communications, and data flows.
- Mendel analyzes mirrored traffic to visualize all devices, hosts, subnets, and services, providing detailed information on communication patterns, protocols, and data flow.
- It automatically identifies critical devices such as Active Directory and email servers, providing essential context for your security teams.
- Detailed information includes hostnames, MAC addresses, users, tags, operating systems, and connections among devices and users.
Advanced Threat Detection
- Utilizing AI and ML, Mendel detects known and unknown threats, including zero-day attacks, APTs, RATs, ransomware, data exfiltration, malware activity, and C&C activity.
- Identifies behavioral anomalies, policy violations, and misconfigurations, including communication with Tor networks.
- Includes an Intrusion Detection System (IDS) with over 85,000 rules to detect known threats.
Protection for IT and OT/ICS Networks
- Monitors both IT and OT environments, supporting industrial protocols from Siemens, ABB, Honeywell, and over 30 office protocols.
- Secures legacy and outdated devices lacking endpoint protection.
- Facilitates IT-OT collaboration through unified network visibility.
Robust Incident Response & Forensics
- Integrates with SIEM, SOAR, XDR, firewalls, and NAC systems.
- Stores historical data for months/years for deep forensic analysis.
- Enables on-demand or rule-based packet capture for in-depth investigation.
Operational Efficiency & Troubleshooting
- Includes NPM and APM for monitoring network and application performance.
- Identifies high response times, retransmissions, slow performance, misconfigurations, and service issues.
- Supports rapid health checks of network infrastructure.
Simplified Management & Deployment
- Web UI with customizable dashboards simplifies operations.
- Pre-configured rules enable quick deployment and SIEM integration.
- Passive monitoring allows agentless deployment with no impact on performance.
- Supports hardware, virtual (VMware, Hyper-V, KVM), and cloud (AWS, Azure, GCP) deployment.
Target Industries & Proven Success (Use Cases)
Use Case: Protecting complex IT and OT/ICS networks from increasing cyber risks, ensuring stability and uninterrupted operation.
Customer: Technical Networks Brno (Czech Republic)
Use Case: Gaining visibility and control over industrial networks to prevent disruptions and protect against targeted attacks.
Customer: (Hidden) — Attack simulation on a cookie factory detected exploit usage, port scanning, and OT network changes.
Use Case: Meeting security regulations, countering state-sponsored threats, and addressing limited personnel resources.
- Hyogo Prefecture Government Office (Japan)
- Office of the Chamber of Deputies of the Parliament of the Czech Republic
- Regional Authority, Olomouc Region (Czech Republic)
Use Case: Securing sensitive patient data, outdated medical devices, and critical infrastructure from modern threats.
- Bulovka Hospital (Czech Republic)
- University Hospital Ostrava (Czech Republic)
- University Hospital Brno (Czech Republic)
- Medium-sized hospital in the CEE region
- Prague City Health Rescue Service
Use Case: Protecting customer data and enforcing security policies in complex infrastructures.
- Empik Group (Poland)
- Kiwi.com (Global Online Travel Agency)
Use Case: Strengthening network protection and enabling real-time threat detection supported by historical data analysis.
Use Case: Helping institutions understand and resolve network issues with clear visualization tools.
Customer: Prague University of Economics and Business (Czech Republic)
Use Case: Protecting confidential client data and maintaining trust under legal compliance demands.
Customer: Kocián Šolc Balaštík (Czech Law Firm)
- Network Security Audit: Fast security checks and in-depth audits of IT/OT networks.
- Operational Monitoring: Ensure reliable operation of services and networks.
- Sensitive Data Monitoring: Monitor and protect critical data from breaches.
- Hybrid/Multicloud Monitoring: Centralized visibility across cloud and on-premise environments.
- SOC Support: Enhance SOCs with analytics, IoT/OT visibility, and threat response capabilities.
Experience the Power of GREYCORTEX Mendel
Don't let cyber threats compromise your operations. Empower your organization with deep network visibility, advanced threat detection, and rapid response capabilities — brought to you by Softprom.
Contact Softprom today for a demo or to learn more about how GREYCORTEX Mendel can secure your network.
Features
Manage, protect, and understand your entire network with GREYCORTEX Mendel.
COMPREHENSIVE NETWORK VISIBILITY
Provides real-time insight into all devices, communications, and data flows.
AI-POWERED THREAT DETECTION
Detects known and unknown threats including zero-day attacks, ransomware, and insider threats.
IT & OT/ICS NETWORK PROTECTION
Monitors and secures both IT and industrial control networks with protocol support.
INCIDENT RESPONSE & FORENSICS
Enables rapid incident investigation with historical data and packet capture capabilities.
OPERATIONAL EFFICIENCY & TROUBLESHOOTING
Monitors network and application performance to identify and resolve issues fast.
SIMPLE DEPLOYMENT & MANAGEMENT
Passive monitoring with flexible deployment options and intuitive web interface.